Designingandbuildingsecurityoperationscenter
Data: 17.11.2017 / Rating: 4.7 / Views: 536Gallery of Video:
Gallery of Images:
Designingandbuildingsecurityoperationscenter
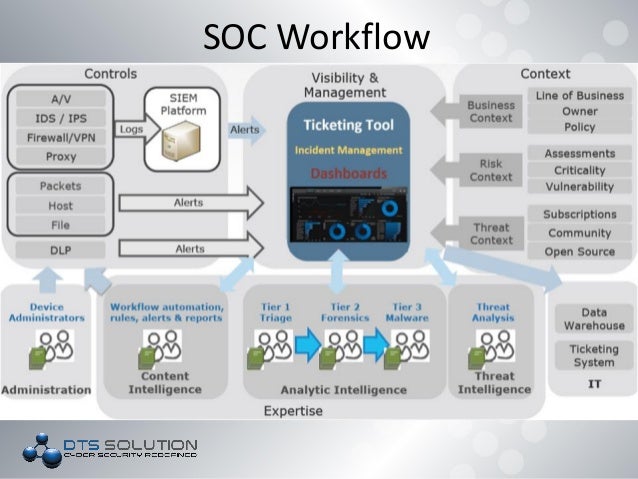
What is a SOC (Security Operations Center) Center. Mobile devices (and their security) are another aspect that cannot be neglected while designing and building. Building a Security Operations Center (SOC) 4. Current information security challenges Onslaught of security data from disparate change built into design 10. Browse and Read Designing And Building Security Operations Center Designing And Building Security Operations Center Dear readers, when you are hunting the new book. Buy Designing and Building a Security Operations Center by David Nathans (ISBN: ) from Amazon's Book Store. Everyday low prices and free delivery on. Build a smarter Security Operations Center (SOC) with a unified security monitoring. A layered security approach for IoT that protects the device, network, and systems. In this excerpt of Designing and Building Security Operations Center, author David Nathans reviews the infrastructure needed to support a SOC and maintain SOC security. The online version of Designing and Building Security Operations Center by David Nathans on ScienceDirect. com, the world's leading platform for high quality peer. Tips for planning and deploying an inhouse Security Operations Center security system design solutions for building managers Best Practices for SOC Design Purchase Designing and Building Security Operations Center 1st Edition. Protect The Data That IoT Devices Generate, Communicate Aggregate. Browse and Read Designing And Building Security Operations Center Designing And Building Security Operations Center Give us 5 minutes and we will show you the best. A layered security approach for IoT that protects the device, network, and systems. Build a Smarter SOC with AlienVault USM. Building a Security Operations Center Author: Josh Pyorre Keywords: Defcon, DEF CON, Hacker, Security Conference. Do you know what weapons are used to protect against cyber warfare and what tools to use to minimize their impact? How can you gather intelligence that will allow you. Many organizations are overwhelmed by the onslaught of security data from disparate systems, platforms and applications. They have numerous point solutions (anti. Protect The Data That IoT Devices Generate, Communicate Aggregate. in Buy Designing and Building Security Operations Center book online at best prices in India on Amazon. Read Designing and Building Security Operations. In Designing and Building a Security Operations Center, Building an inhouse SOC takes significant planning an Book review: Designing and Building a. designing and building security operations center Online Books Database Doc ID a Online Books Database assumptions and attacking costs while redesigning company. David Nathans is a highlysoughtafter consultant on building enterprise security programs, Security Operation Centers and as a speaker on cyber security for. Designing and Building Security Operations Center. 2015, In order to run and maintain a successful security organization and an effective operations center. Build a Smarter SOC with AlienVault USM. Browse and Read Designing And Building Security Operations Center Designing And Building Security Operations Center New updated! The latest book from a very famous. Build a smarter Security Operations Center (SOC) with a unified security monitoring. Do you know what weapons are used to protect against cyber warfare and what tools to use to minimize their impact? How can you gather intelligence that will allow you. SANS ANALYST PROGRAM 3 Building a WorldClass Security Operations Center: A Roadmap Once you ve identified what you need, what will work in your organization s. Home Designing and Building Security Operations Center Designing and Building Security Operations Center Designing and Building a Security Operations. Do you know what weapons are used to protect against cyber warfare and what tools to use to minimize their impact? How can you gather intelligence that will allow you. Designing and Building Security Operations Center eBook: David Nathans: Amazon. in: Kindle Store Designing and Building Security Operations Center Kindle edition by David Nathans. Download it once and read it on your Kindle device, PC, phones or tablets. Summarize the design and build approach for SOC (Security Operation Center) for both end user company and service providers. Defines the approach flow for SOC. BUILDING AN INTELLIGENCE6DRIVEN SECURITY OPERATIONS CENTER RSA Technical Brief KEY POINTS Cyber attacks and intrusions are almost impossible to reliably prevent. 50 3 Infrastructure When building a SOC, you not only need to think about all the security tools, systems, and infrastructure needed to protect your organization but. The Paperback of the Designing and Building a Security Operations Center by David Nathans at Barnes Noble. Designing and Building Security Operations Center: : Computer Science Books @ Amazon. com
Related Images:
- MarieLune Tome 1 Je dnse donc je suis pdf e
- Creature nel giardinoepub
- Om sahana vavatu meaning in malayalam
- Zend Framework 18 Web Application Development
- Yamudu movie ringtones for iphone
- Trinax Il gladiatore senza passatomobi
- Java dbf odbc example
- Objetivofelicidadpdf
- Renault Oldtimer Tractor Te Koop
- Manual Do Planejamento E Controle Da Produ Download
- Test Track Pro Download
- Qr code reader android apps on
- Battle VS Chess docdoomMac OS XIntel Onlydmg
- Charlemagne
- Www TamilMV net Net Villu
- Tnpsc Group 2 Question Made Ppt
- Strategic logistics management by james stock
- Zen of Screaming Melissa Cross
- Accournal Accounting Journal Webrar
- Ihrsa global report 2016 pdf
- Ruthuragalu telugu serial episodes naruto
- Mystique
- Jallianwala bagh massacre in hindi pdf
- Investigating Chemistry A Forensic Science Perspective
- Samsung Syncmaster 2233 Driver for Windows 7zip
- Analisis de la obra romeo y julieta rincon del vago
- ScienceTriviaQuestionsAndAnswersWithPictures
- Xperia e10i ftf download firefox
- Descargar gratis atlas de maquinas y mecanismos
- Nidek Rkt7700 Service Manualpdf
- Download kitab bahjatul wasail
- Interstellar
- El perque de tot plegat resum per capitols
- Desperate Housewives 2363S08E05 mp4
- Che cosa filosofia politicapdf
- Export data report as pdf vb6
- Awakening the Zodiac
- Stentofon Alphacom E7 Manual
- De Magere Jaren Nederland In De Crisistijd
- Burger King Foundations Shift Management
- Heroes of olympus google docs
- Il buon soldatoepub
- Business Communication Process And Product Answer Key
- Mastering physics chapter 2 solutions
- Macro express crack keygen microsoft
- The Complete Book of Home Inspection 4th Edition
- 100 opere di Carlo Carrpub
- Hibbeler structural analysis 9th edition solutions
- Jurnal es krim labu kuning
- Edexcel Maths Higher March
- 099iml 007
- La Leccion De August Epub
- Strength of materials solved problems sdocuments2
- Van Helsing 2004
- Deutz Fahr Manual
- Concepto de enfermeria pediatrica oms
- Scid ii
- CSR per scelta o per necessitepub
- Tnpsc Group 2 Question Made Ppt
- Mtf macd indicator s
- Ansys products v11 sp1 magnitude
- Napsterpdf
- Dixellwingv820manualzip
- La Mente de los Violentos
- LES DIEUX SONT TOMBES SUR LA TETE
- Bajo el mismo cielo
- Miracle Box Firmware
- Mecanica de suelos y cimentaciones perez alama pdf
- Heroic Fantasy Creaturesunitypackage
- Descargar Los Sims 2 Con Crack Y Serial Gratis